Introduction:
Threats associated with technology are evolving along with it. In particular, phishing assaults are getting more sophisticated and pose a serious threat to people’s online security. We’ll dive into the realm of phishing in this blog article, looking at typical strategies used by hackers and offering helpful advice on how to spot and stay clear of these dishonest schemes.
What is Phishing?
Phishing is a malicious tactic used by hackers to fool people into disclosing private information, including credit card numbers, passwords, and personal information. It is imperative that you comprehend the standard methods used by phishers in order to defend yourself against these assaults.
-
Email Spoofing:
An attack technique that is frequently used involves impersonating reputable emails from reliable sources. This entails creating the appearance of authenticity through the use of persuasive language and logos. Check emails carefully for grammatical errors, formatting issues, or inconsistent sender information.
2. Phony Website:
Phishers frequently construct phony websites with URLs that closely mimic real websites. Users might be easily tricked into inputting important information by these dishonest URLs. Hover your cursor over links to see the destination URL before clicking on any of them. Any misspellings or discrepancies that could point to a phishing attempt should raise suspicions.
3. Social Engineering:
This is a strategy that uses psychological tricks on people to coerce them into disclosing private information. This may entail assuming the identity of reliable people or instilling a sense of urgency to encourage swift action. Remain alert and inquire about the validity of requests for private information, particularly if they appear out of the ordinary or unexpected.
4. Malevolent Attachments:
Phishing emails could include malicious attachments that, if you open them, might take over your device and steal private information. Refrain from opening attachments from unexpected or unknown sources. Make sure the sender is legitimate before downloading any files.
Identifying Phishing efforts:

Now that we are aware of typical phishing tactics, let’s investigate how to spot possible phishing efforts so that we can take precautions.
Recognizing Phishing Attempts:
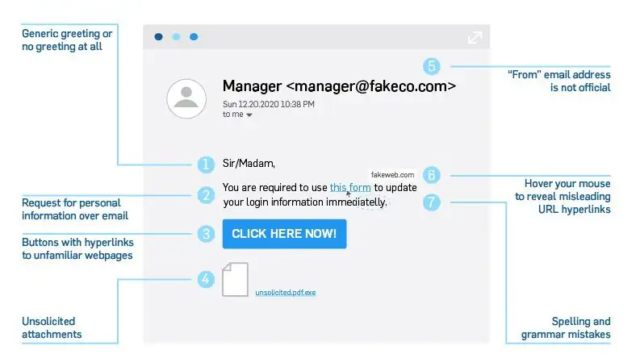
Now that we understand common phishing techniques, let’s explore how to recognize potential phishing attempts and protect ourselves.
-
Verify Email Addresses:
Prior to responding to an email, make sure you have verified the sender’s email address. Official domains are used by legitimate organizations; any variation from this should trigger red flags. Email addresses that seem updated or have minor spelling errors should be avoided.
2. Examine Email Content:
Phishing emails frequently have subliminal cues that you can look out for. Check for misspellings, odd wording, or cliched greetings. Since legitimate firms usually communicate in a professional manner, any discrepancies should be taken seriously.
3. Refrain from Clicking on Unexpected Links:
If you get an unwanted email with a link, fight the impulse to click it right away. Alternatively, use your browser to independently access the official website by entering its URL. This guarantees that you are seeing the authentic website and are not a victim of a phishing scheme.
Advice for Preventing Phishing Attacks:
Taking proactive steps will greatly improve your online security, in addition to identifying any phishing efforts.
-
Turn on Two-Factor Authentication (2FA):
Adding 2FA gives your accounts an additional degree of protection. A second form of authentication would still be necessary for a cybercriminal to access your account, even if they managed to get their hands on your password.
2. Maintain Updating Software and Antivirus:
Update your operating system, apps, and antivirus program on a regular basis. Security patches that guard against the most recent malware and phishing attacks are frequently included in software updates.
3. Educate Others and Yourself:
Keep up with the most recent phishing techniques and let your friends, family, and coworkers know about them. A knowledgeable community is better able to identify and prevent phishing attempts.
4. Keep Up with Phishing Trends:
Since cybercriminals are always changing their strategies, it’s important to keep up with the most recent phishing trends. Get regular updates from reliable sources, follow cybersecurity professionals on social media, and subscribe to security blogs. Gaining an understanding of new dangers will enable you to spot phishing techniques and modify your defenses appropriately.
5. Use Email Filtering Software:
If you want to prevent phishing emails from ever getting to your inbox, think about utilizing email filtering software. These programs look for trends linked to phishing attempts by analyzing email content, attachments, and sender information. Although not infallible, these filters offer an extra degree of defense against typical phishing attacks.
6. Be Wary of Pop-Up Windows:
Phishers frequently utilize pop-up windows to deceive victims into inputting personal data. These pop-ups could imitate official forms or login windows. Unexpected pop-ups should always be regarded with caution, especially if they ask for personal information or login credentials. To confirm the validity of the request, close any pop-up windows and use your browser to visit the official website.
7. Keep an Eye on Your Accounts Frequently:
Keep a close eye out for any unusual activity on your email accounts, bank accounts, and other online identities. Take immediate action to safeguard your accounts if you discover unusual changes or unauthorized activity. A phishing attack’s potential damage can be reduced by early identification.
8. Use a Virtual Private Network (VPN):
When accessing online services, a Virtual Private Network (VPN) adds an additional degree of security by encrypting your internet connection. Your data is more protected by this encryption from possible cybercriminals’ interception. A VPN is especially helpful in preventing man-in-the-middle attacks, which can result in phishing events, when utilizing public Wi-Fi networks.
9. Educate Your Team at Work:
If you work in a group or team, inform your coworkers about the dangers of phishing and the best ways to avoid it. To make sure that everyone is informed about the most recent dangers and knows how to respond effectively, hold frequent cybersecurity training sessions. Establishing a cybersecurity-aware culture at work is a team effort that fortifies the entire defense against phishing scams.
10. Report Suspected Phishing Attempts:
Notify your email provider or the IT department of any unusual emails you receive. The majority of email services include reporting tools for phishing attempts. By reporting such events, you safeguard others and yourself by joining the collaborative effort to uncover and eliminate phishing campaigns.
Conclusion:
Phishing attempts are a persistent menace in today’s connected world, but you may guard against falling victim to these dishonest tactics by being aware of them and exercising caution. Through comprehension of prevalent phishing methods, identification of possible phishing endeavors, and execution of preemptive security protocols, one will be more adept at securely traversing the digital terrain. Always remember that being knowledgeable and ahead of cybercriminals is the key to being safe online.
Also Read: The Evolution of Cybersecurity and AI
